Chart your path towards resilience with Intentional Cybersecurity
Helping clients build resilient businesses through stronger cybersecurity programs.
Intentional Cybersecurity:
From Compliant Value Preservation to Resilient Value Creation
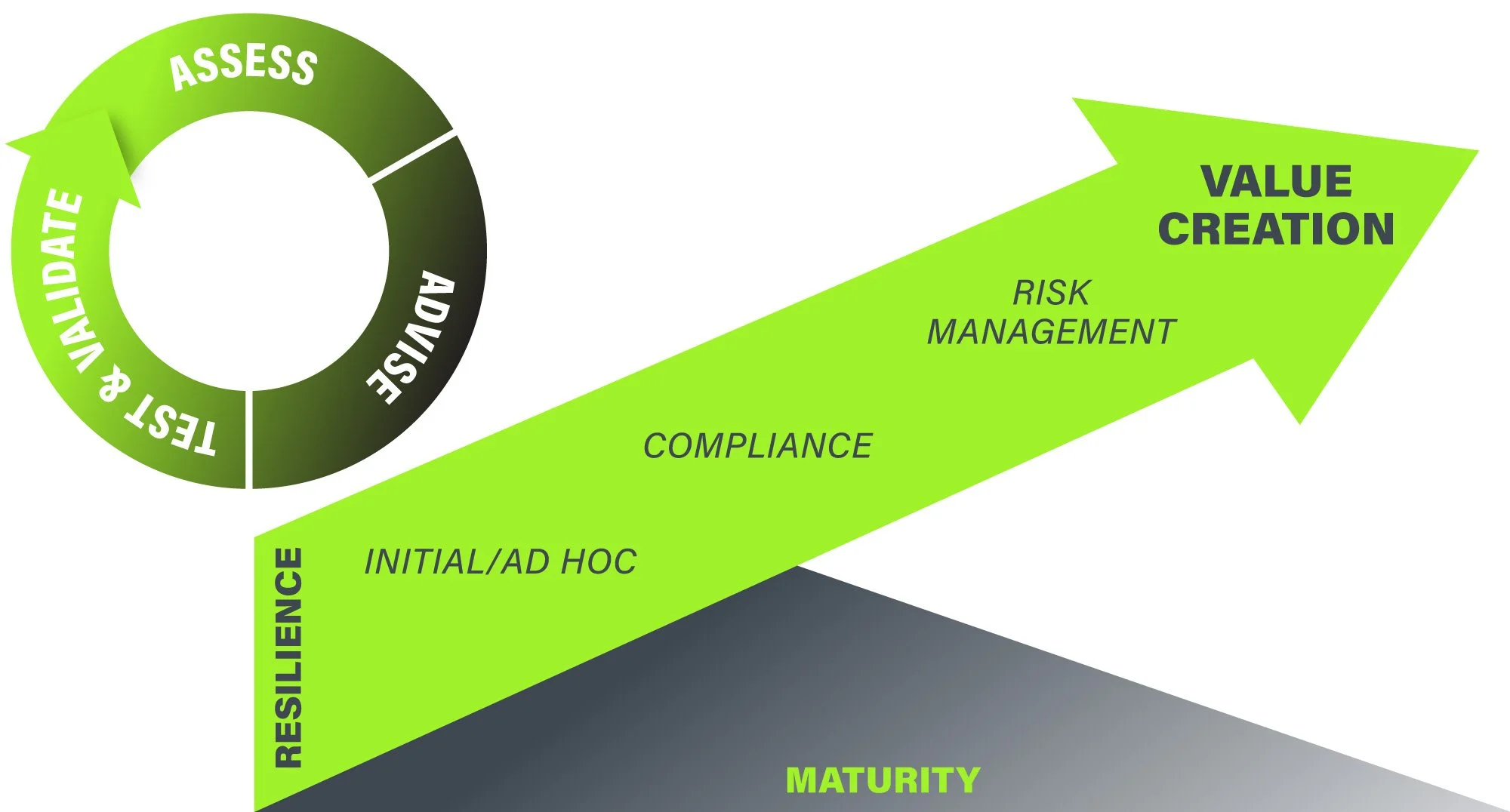
Intentional Cybersecurity is your partner in navigating the complex landscape of compliance and digital protection. We go beyond compliance exercises focused on preserving business value; we help transform your cybersecurity program into a strategic asset that drives value creation over time.
The Intentional Journey to Cyber Resilience
Our Services
Assessment Services
Comprehensive assessments, including cyber risk, regulatory compliance, and maturity assessments help you identify risk, evaluate regulatory compliance, and strengthen your organization’s overall security posture and resilience.
-
We guide clients in understanding and managing their overall risks by conducting comprehensive cyber risk assessments. Our senior security professionals employ decades of experience in technology, incident response, and cybersecurity to identify technical, operational, and procedural risks, prioritize them, and deliver detailed recommendations for effective remediation. By aligning our assessments to your preferred security framework, such as NIST Cybersecurity Framework, we provide a comprehensive analysis that empowers you to protect your valuable assets and make informed decisions for a resilient security posture.
-
Our comprehensive HIPAA Risk Assessments offer a dual benefit of achieving regulatory compliance with the HIPAA Security Rule while effectively managing real cyber risks faced by healthcare organizations. By assessing administrative, physical, and technical safeguards, our engagements provide a holistic view of your compliance status and identify areas for improvement, allowing you to proactively address vulnerabilities and mitigate actual cyber risks. With our approach, you can achieve regulatory compliance and strengthen your organization's security posture in a single engagement, ensuring the protection of sensitive health information and maintaining trust with patients.
-
Our Cyber Due Diligence service equips deal teams with the confidence to navigate the digital landscape of Mergers & Acquisitions by conducting a comprehensive assessment of a target company's cybersecurity posture. We analyze security controls, processes, and technology, identifying potential vulnerabilities and risks that could impact the success of the deal. Our actionable recommendations enable clients to make informed investment decisions, manage cyber risks effectively, and leverage cybersecurity for value creation post-transaction.
-
Our Compliance & Maturity Assessments enable organizations to benchmark their compliance against industry-specific frameworks such as NIST Cybersecurity Framework or Center for Internet Security Controls while strategically advancing their security posture. With our expertise in aligning stakeholders, prioritizing efforts, and delivering outcomes, we help clients achieve desired compliance or certification, such as HIPAA, CMMC, SEC, NYDFS, SOC 2, and more, while building resilient capabilities that enhance overall security and regulatory readiness. Our thoughtful approach ensures that compliance and security efforts work hand-in-hand to protect your organization and meet industry standards.
Advisory Services
Our senior advisory services team leverages decades of in-house and consulting experience to provide advisory services that encompass strategic planning, policy development, technical guidance, CISO support, incident response planning, and security awareness training to provide thoughtful, right-sized support to your business needs and risk profile.
-
Our Strategic Advisory Services offer virtual Chief Information Security Officer (vCISO) expertise to keep Boards, Executive Teams, and technical resources aligned and engaged in cybersecurity matters. With our seasoned team of experts, we provide customized and cost-effective solutions, including strategic planning, risk management, policy development, and compliance support, helping businesses navigate the complex cybersecurity landscape with confidence and ensure effective governance at the executive level.
-
Our Third-Party Risk Management service enables clients to establish and operate robust programs for managing cybersecurity risks associated with vendors, partners, and suppliers. Through comprehensive assessments, we analyze information security policies, controls, and incident response capabilities, providing a clear understanding of third-party risks. With our expertise, clients can prioritize risk mitigation efforts based on the level of risk posed by each relationship, ensuring effective management and protection of their valuable assets across the supply chain.
-
Our Incident Response Plans & Table-Top Exercises ensure organizations are well-prepared to respond swiftly and effectively to cyber incidents. We develop tailored incident response plans, aligned with specific needs and risks, and conduct simulated tabletop exercises to test response readiness. Through our real-world experience and comprehensive feedback, clients can identify areas for improvement, meet compliance requirements, and build a culture of resilience, minimizing the impact of security incidents and safeguarding their assets and information.
-
Our Technical Advisory Services provide tactical remediation assistance to IT teams, along with support for attorneys and executives in evaluating technical solutions, implementation requirements, and risk management goals. With our expertise and guidance, we assist in navigating complex technical challenges, recommending effective solutions, and aligning them with your organizational objectives to achieve optimal outcomes while ensuring robust risk management practices.
-
Our Security Awareness Training service equips your employees with the knowledge and skills to become the first line of defense against cyber threats. Through engaging and interactive training sessions, we empower your workforce to recognize and respond to security risks, fostering a culture of cyber awareness and resilience.
As an optional bundled offering to meet regulatory compliance, this service is often bundled with annual Risk Assessments and Penetration Tests to ensure a proactive and holistic approach to safeguarding your organization's critical assets.
-
Our Policy Creation service helps organizations establish or enhance their cybersecurity policies, ensuring a solid governance foundation for a mature cyber program. Whether creating new policies or maturing existing ones, we work closely with clients to develop comprehensive and tailored policies that align with industry best practices, regulatory requirements, and their specific organizational needs, enabling them to effectively manage and mitigate cyber risks.
Testing & Validation
Proactively manage cyber risk and ensure controls are implemented as intended with our rigorous penetration testing, cloud security assessments, and vulnerability scanning services, allowing you to identify vulnerabilities, take intentional actions to mitigate risks, and fortify your defenses against evolving threats.
-
Our Penetration Testing and Validation service safeguards your organization's security by identifying and reporting on vulnerabilities within your network, applications, and web systems. Our ethical hackers employ sophisticated techniques to simulate real-world attacks, providing a comprehensive report with actionable recommendations to mitigate risks. We go beyond commodity tools to give our clients a customized, intentional approach paired with expert insights so you can proactively protect your data, customers, and maintain a more secure environment.
-
Our Cloud Security Assessments for Microsoft365, Azure, AWS, and Google ensure that your cloud environments are architected and deployed in alignment with best practices, while considering the robustness of your SDLC/DevOps teams. Our assessments provide a comprehensive evaluation of your cloud instances, identifying potential security vulnerabilities, and offering recommendations to enhance the overall security posture of your cloud infrastructure. With our expertise, you can confidently leverage the power of cloud services while maintaining strong security controls and protecting your valuable data.
-
Our Vulnerability Assessments offer a thorough analysis of your organization's security posture by identifying potential risks and vulnerabilities across various technologies and platforms. Our expert team conducts comprehensive assessments of network devices, operating systems, and applications, providing you with actionable recommendations to remediate vulnerabilities and enhance your overall security. With our meticulous approach, you can proactively strengthen your defenses, minimize security risks, and safeguard your valuable assets from potential threats.